CREATING A CULTURE OF SECURITY AWARENESS
The Information Security Office provides policies, tools and processes to protect the information resources of the University of Arizona, using a shared responsibility model.
The Information Security Office
ISO helps protect the University’s computing and information assets from emerging security threats and ensures compliance with laws, regulations, and University policies. ISO has implemented important practices and monitoring to protect the institution and its constituents against continuous threats. This multifaceted diagram demonstrates some of these safeguards in action as they protect against ransomware.
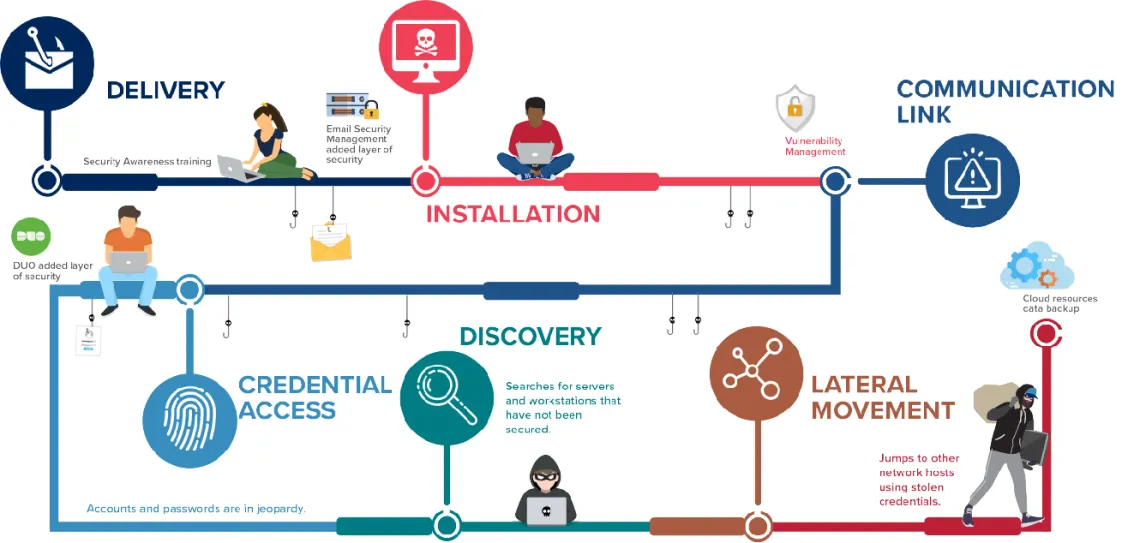
Programs to Protect Against Every Step of an Attack
Delivery
The University’s Information Security Awareness Training was migrated to the new EDGE Learning platform in FY2020.
Faculty and staff receive frequent, targeted communications and tips to help them avoid clicking on malicious links or attachments.
Layers of protection remove threats before they arrive at email inboxes.
Security devices employed in centralized email services scan emails against known bad hashes and can detonate bad payloads when located.
Installation
University units participate in the Risk Management Program to evaluate and apply appropriate security controls to help detect and prevent the execution of malicious code on laptops, desktops, servers and other endpoint devices.
Sophos, offered centrally to all faculty, staff
and students, provides antivirus detection and behavioral analysis detection. Cryptoguard is an additional tool with alerts configured that can help reverse attempts at encryption.
Communication Link
Firewall is a device that contains an updated list of known malicious IPs and Addresses.
Malicious domains are monitored and blocked.
Credential Access
The NetID+ program provides access to the multi-factor authentication solution which adds a layer of protection
when your password has been hacked. This second layer of authentication is required before an attacker can gain access to an account with compromised credentials.
Discovery
Network Segmentation creates separation between various units/colleges on the IP Address level. Sensitive data may exist on separate segments as well. (Maturity of implementation varies across the University.)
Lateral Movement
Participants in the Information Security Risk Management program are guided to evaluating and applying appropriate access controls. These controls restrict access to sensitive information to only those who need to know in performance of their job function.
Two-factor Authentication helps to prevent lateral movement.
Network Segmentation helps to prevent lateral movement.
Impact
Information Security Incident Reporting and Response Policy requires units to coordinate with the Security Operations Center to mitigate the impact of any realized risk scenarios.
Incident Response Plans developed by units include seeking help from professionals in the Information Security Office to help users and units when there is a cybersecurity event.
Cyber Insurance protects against financial loss from paying ransom.
