Network Technologies
UArizona's World Class Network
Network authentication architecture at the University of Arizona has created a new chapter in how networked devices connect. It is a transformation for which we are considered a vanguard in this technology but what may soon become the standard for our peer universities too.
In the world of authentication, devices such as laptops, smartphones and tablets, reach out to their domain authenticator to establish a secure connection to the local network and through it, their applications, networked resources and the internet become available to them. This authentication process is like a handshake that once established, allows the device to pass data to and from other resources connected to the network.
This explanation is very basic—what our Managed Cloud Services (MCS) team has created is much more sophisticated. UITS began the move to cloud services in 2017. Known as the Cloudaprise project, the scope was to shift enterprise applications off locally housed (on-premise) servers into a cloud environment. This created the capacity for flexibility (elasticity) in processing usage based on demand during heavier activity such at the start of fall semester and spring registration. It also provided a much greater amount of storage capacity.
The university’s network authentication service is Microsoft’s Active Directory. The original instance of this service was codenamed Catnet 1.5, built to primarily authenticate the enterprise applications and networked devices—most of which were wired devices. The introduction of WiFi (wireless networking) nearly 15 years ago changed the network landscape. As researchers, students, faculty and staff moved further into the use of WiFi to connect their resources onto the university’s networks there was a shift in the physical and virtual infrastructure and increased demand for a different level of authentication architecture.
Once students, faculty and staff returned to campus after the pandemic, this heightened need for a more robust authentication process inspired the cloud management team to think beyond traditional practices. Moving authentication into the cloud was a huge step that no other university had tried and took an industry level of expertise the CIO Division has been fortunate to retain.
To achieve this authentication method, the UITS architecture had to be temporarily isolated from the broader campus community to prevent interference with other university IT systems and processes as development moved forward. Once the system separation was made, UITS was able to deploy a newer network architecture into the AWS cloud, which gave it the elasticity and scalability being sought. The subsequent upgrade to the rest of the university infrastructure and move to CatNet 2.0 was successfully completed in 2023. The team overcame tremendous skepticism in the idea of authenticating WiFi services in data centers hundreds of miles away. Jason Sullivan, the University of Arizona’s network architect reflects, “but of course light travels quite quickly, and we have very redundant service between here and there.”
As the rest of University’s IT departments migrated to the newer, more robust CatNet 2.0 in the cloud, the scalability of the architecture proved itself. “If we look at the failure rates 2 years ago, prior to this innovative architecture change today, a tremendous amount of our traffic was failing because the on-prem service was poorly architected for a multi-use infrastructure.” Jason went on to explain, “And now it’s architected well. It’s highly redundant, and we have no authentication problems.” A slight caveat to this is there could be WiFi authentication failure when someone moves out of range of one access point and in range of another during authentication.
The following page shows a simplified graphic mapping the redundancy of the university’s internet connectivity and subsequent cloud authentication process. Access to the internet comes from two primary sources, Internet1 via multiple AWS availability zones across the U.S. and the Internet2 accessible via the Sun Corridor Network. Both sources have public and private secure internet access redundancies to the university. Additional redundancy is available from commercial Internet providers, should it be needed.
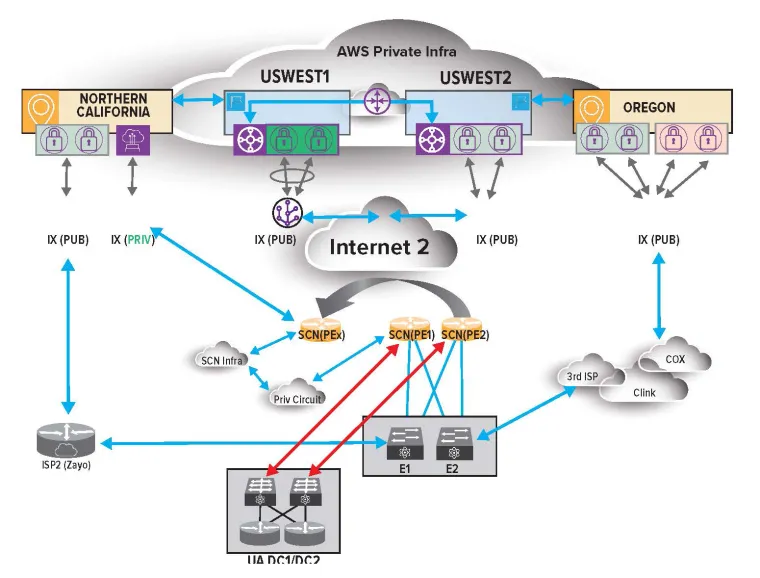
SUN CORRIDOR NETWORK
The Sun Corridor Network is Arizona’s regional research and education network, and it is the University of Arizona’s connection to Internet2. Internet2 provides a secure, high performance, low latency network built to serve a national, globally interwoven technology infrastructure and collaboration among the nation’s researchers, scholars, and learners. Founded in 2013 by the three state universities, ASU, NAU and UArizona, the Sun Corridor Network created high speed connections with each university and with Internet2.
FY23 Metrics
NETWORK DEVICES
Network Core
42
Dist. Network
3.8K
WIFI Access Points
11K
Unique Wireless Devices
118K
Unique Wired Devices
47.3K
SERVICES
- Network Core & Internet2 ISP
- Campus Data Network
- Voice Services
- Network Management
- Network & Data Center Operations
