BUILDING A ROBUST MATURITY MODEL
Implementation of NIST SP 800-171 Elements
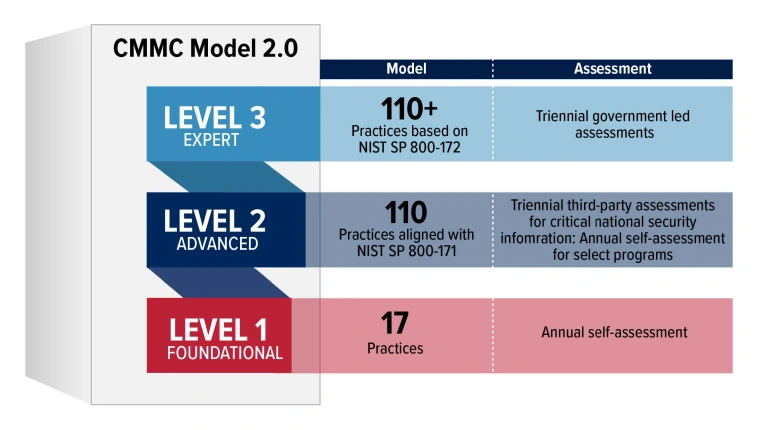
In 2024, the Information Security Office (ISO) team began introducing the university IT community to the adoption of a more robust security model that includes elements from the U.S. Department of Defense’s (DoD) Cybersecurity Maturity Model Certification (CMMC). Narrowing that vision to the principles of the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 enhances the University of Arizona’s cybersecurity posture, which began with the development and standardization of UASecure as the risk assessment and planning tool.
UASecure was established as the risk assessment tool in 2018. The Information Security Risk Management Program (RMaP) serves as the central program for providing an integrated, prioritized approach to addressing risk to University Information Resources. It aligns with the University’s business and academic objectives. RMaP is implemented through UASecure, the official system of record for RMaP. Currently, UASecure reports a success rate for 100% of academic and administrative units across the university that have completed at least one (1) approved security plan in UASecure. For these units, their successful participation makes it easier to implement the next level of cybersecurity more achievable. UASecure addresses compliance with ISO policies through 55 questions that map to NIST SP 800-53 objectives.
“CMMC was developed by the U.S. Department of Defense and has become the gold standard for other agencies to adopt in protecting information categorized as Controlled Unclassified Information (CUI),” explains Wendy Eppley, Principal Analyst, Information Security Office-Governance, Risk and Compliance. “CMMC is a very complex framework specific to the DoD and applicable to Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).”
The university will use NIST SP 800-171 as the standard for cybersecurity practices, incorporating CMMC elements. “With so many federal agencies now adopting the NIST SP 800-171, it has become the primary standard we are adopting to help units to mature their cybersecurity practices. These controls will ensure that university information and resources are protected and consistent with the policies of various government agencies.”
The Initial response to enhanced cybersecurity practices may feel overwhelming to some IT professionals. Epley reminds us that many of the information security processes already in place at the university align with the federal government’s model. “While the university as a whole is a long way from the upper levels of CMMC equivalency, there are several units on campus that are likely very close to achieving them.”
Implementing of the ISM’s tiered structure will take time. The first step in this process will require units to identify their Information Resources, inventory their assets, and scope the boundaries for the key focus area to meet the controls outlined in NIST SP 800-171. Once the scoping process is complete, units will address the foundational cybersecurity practices specified by NIST SP 800-171. “The objectives for the foundational cybersecurity practices are very basic cybersecurity hygiene,” explains Wendy. “This level is not difficult to achieve, as many have already standardized their security practices through the annual assessment in UASecure.”
The university’s Information Security Maturity (ISM) program will utilize the Cyturus Compliance and Risk Tracker (CRT) to assess NIST SP 800-171 compliance and manage remediation plans. In 2023, Cyturus partnered with The Cyber AB, the official accreditation body of the CMMC Ecosystem, to provide the CRT to Registered Practitioner Organizations (RPOs) equipping them with the essential readiness, assessment, and compliance tools for CMMC compliance. Assessments will be conducted against the scoped Information Resource with support from the ISO-GRC team throughout the year. Units will still need to complete their annual assessments in UASecure until the in-scope Information Resource has been fully assessed in Cyturus. This means a Unit may maintain multiple security plans in UASecure or manage various engagements within Cyturus.
FY24 Metrics
FIREWALL (BORDER) BLOCKS
Firewall Blocks Per Day
300M
SECURE MONITORING
Log Aggregation
200TB
Phishing and Spam Emails Blocked Per Day
0.5M
RISK MANAGEMENT
Percent Units Completed FY23 Plans
100%
Number of FY23 Completed Security Plans
200
SECURITY AWARENESS TRAINING
FT Faculty/Staff Participation in Training
100%
Application Developer Training Participation
99.20%
